Restoring a Pharma Hacked WordPress Site (WP 3.4)
I’ve been working on my Professor K’s blog and found that it had been hacked. It was kind of strange how I found that it was hacked; while trying to install a new plugin through the backend, the plugin window that pops up was filled with weird pharmacy links and images. I thought that was strange, so I searched the ends of the internet for answers. It is apparently a well-known and common exploit called the Pharma Hack. One of the best ways to see if you have been hacked is to run the Sucuri Sitecheck scan on it. It’s free and will show you what pages are currently hacked.
There are lots of how-tos and guides online, but most of them are outdated. The pharma hack has evolved (1,2,3).
I first tried to fix the issue by searching my wordpress directory for offending files, usually containing the string “base64_decode”. I used the following command in the wordpress directory
$ grep -o -H -n -r "base64_decode" .
There were several files that did not appear to be real wordpress files, so I completely replaced the wp-includes directory with the code from the latest WordPress release. This didn’t help.
I installed the Wordfence plugin. It’s a fantastic plugin and does well at finding malicious files, however it appears that the pharma hack removes the plugin entirely! It is still very helpful at finding affected files.
After the malicious files kept coming back, I continued by hardening my wordpress installation. The hack returned.
Desperate, I completely reinstalled the website from scratch, using the same database, copying back the uploads file (which contained no php code), reinstalling the plugins from wordpress directly, and using only the default themes plus my clean child theme. The hack returned!
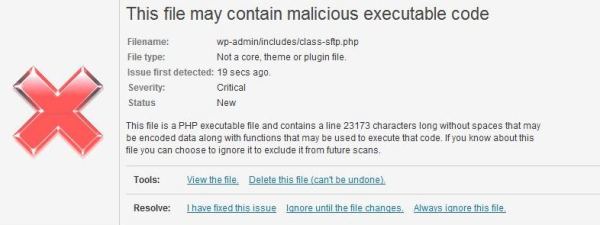
Today I am looking at the files that Wordfence found either unrecognized, modified core files or malicious:
wp-admin/includes/class-sftp.phpwp-includes/native.phpwp-includes/class-wp-error.phpwp-includes/legacy.php
It looks like the modified core file, class-wp-error.php, is what the hackers use to bootstrap their exploit, because the only difference between the clean file and the compromised file is this single line:
@require_once ('native.php');
native.php is an injected file and is full of obfuscated code.
The code is so obfuscated in fact that I can’t really follow how the other files relate, except that legacy.php seems to be what grabs the pharma code.
What I did is, in order,
- Restore
class-wp-error.phpandchmodit to444(not sure if that will help protect it but worth a shot) - Deleted the other files Wordfence found
- Ran another Wordfence scan to make sure they’re all gone and clean
- Hardened my site again
- Removed FTP access and changed the SSH/SFTP password
- Installed Better WP Security (known to play well with Wordfence)
- Reinstalled all my plugins (to be safe)
- Wait
I have a bad feeling that the site is still hacked and it’s only a matter of time before those malicious files appear again. I’ll update this if the site is still hacked.
Update 6/25/2012:
The site appears to be clean. I’ve uploaded copies of the 4 files that were marked as malicious or unkown here.
Comments
Leigh
Yeah Wordfence did find a lot of stuff on several of my clients sites on several different web hosts, but they all got hacked anyway. I think it is not really a security plugin and is just a scanner. Got some great gimmicks in it thought that really impress clients. ;) But they are not too impressed with Wordfence after their websites get hacked. LOL I've never had much success with Better WP Security either. It is also good as a checklist plugin, but it doesn't stop hackers either. Let me know if you find a WordPress security plugin that really works. I'd love to know which one it is. Thanks.
bradford
Will do - after doing the steps in this post the hack hasn't returned. What really surprised me was that it returned after I completely wiped out the site and started over. I suspect some of the steps I took in Better WP Security helped but I can't be certain.
Wilson
Professor K's site is not clean as of August 2012. I just searched via Google and there are multiple pages still selling Cialis in the titles!!!
bradford
Wilson, thanks for your comment. I did a scan (http://sitecheck.sucuri.net... and that came up clean, and when I google "charlesknutson.net" I don't see any immediately apparent pharma results. What search string did you use?
Xyborg
Thank you so much! this post helped me today to find this motherf**kers... I have been with this since the last sunday. In my case the infected files were inside the wp-admin/includes folder and function _1716395676 was inside wp-settings.php
bradford
It's ridiculous how hard it is to remove. That's one of the problems with using a CMS/Blogging platform as ubiquitous as wordpress.
Xyborg
It's incredible.. I continue finding blogs hacked using this same files or method... What I couldn't find yet is how are doing this guys to get inside a website which is/was supposed to be up to date and the server didn't detected any intrusion from their side. Minutes ago, I found one file identical (the md5 hash was the same) to the one you shared.
john
The pharma hack seems to have evolved further and now infects non-wp sites as well. All the sites I host on a shared server have been infected. Short of visiting the witch doc, I've tried everything recomended - no use. It creates a directory called "cockies" with a bunch of .php files in it and in the root it injects code into the .htaccess file and also creates a really nasty "common.php" (which I've not been able to crack). I've not been able to find triggers - so far.